Describe Domain Name System.There are two types of client/server programs.First is used directly by the user, such as e-mail, Second supports other application programs. The Domain Name System (DNS) is a supporting program that is used by other programs such as to find the IP address of an e-mail recipient. | ||||||||||
Describe Hierarchical Namespace.In a hierarchical name space, each name is combination of several parts as:Type of the organization. Name of an organization. Departments in the organization. A central authority can assign the part of the name that defines the nature and name of the organization. The other things of the name the organization provides itself. The organization can add suffixes (or prefixes) to the name to define its host. The company need not worry about the prefix if it is same as that of another organization because, even if part of an address is the same, the whole address is different. Example: Suppose central authority has given names ABC.com and XYZ.com to two separate organization but these organization can add prefix as career so the name becomes career.XYZ.com and career.ABC.com. The names are unique without the need for assignment by a central authority. The central authority controls only part of the name, not the whole. 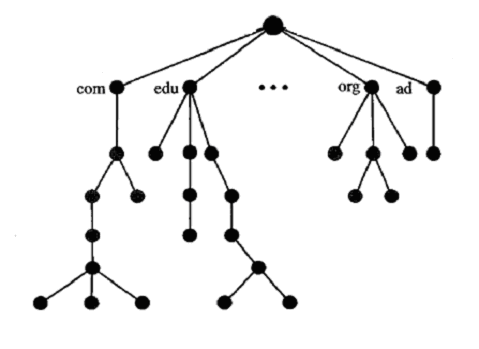 | ||||||||||
Define Fully Qualified Domain Name and Partially Qualified Domain Name.In hierarchical name space, names are defined in an inverted-tree structure with the root at the top. The tree can have only 128 levels: level 0 (root) to level 127.Each node in the tree has a label, which is a string with a maximum of 63 characters. The root label is a null string (empty string). In this tree, all the labels have different name, which guarantee the uniqueness of the domain names. A full domain name is a sequence of labels separated by dots (.). The domain names are always read from the node up to the root. Fully Qualified Domain Name If a label is terminated by a null string or empty string, it is called a fully qualified domain name (FQDN). Partially Qualified Domain Name If a label is not terminated by a null string, it is called a partially qualified domain name (PQDN). A PQDN starts from a node, but it does not end with the root. What is transmission impairment?Signals need transmission media for travel from one point to another. Transmission media are not perfect because it provides resistance. The imperfection causes signal impairment. This means that the signal at the beginning of the medium is not the same as the signal at the end of the medium. What is sent is not what is received. There are three causes of impairment are attenuation, distortion, and noise.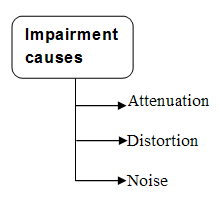 | ||||||||||
Describe attenuation, distortion, and noise in brief.Attenuation: When a signal travels through a medium, it loses some of its energy due to resistance of the medium. This loss of energy is called Attenuation. This is the reason why a wire carrying electric signals gets warm. Some of the electrical energy in the signal is converted to heat. To overcome for this problem, amplifiers are used to amplify the signal.Unit of the decibel is used to find out if a signal has lost or gained strength. The decibel (dB) measures the relative strengths of two signals or one signal at two different points. If decibel is negative then a signal is attenuated and if positive signal is amplified. Formula: 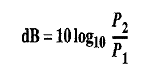 Where PI and P2 are the variable and the powers of a signal at points 1 and 2, respectively. Distortion When the signal travels through the medium from one point to another it may chance to change the form or shape of signal. It is called distortion. Distortion can occur in a composite signal, made up of different frequencies. Each signal component has its own propagation speed through a travelling medium and, therefore, its own delay in reaching at the final destination. Means signal components at the receiver have phases different from what they had at the sender. Noise The third cause of impairment is Noise. Following types of noise are possible. -Thermal noise. -Induced noise. -Crosstalk noise. -Impulse noise. These noise may corrupt the signal. Thermal noise is produced due to the random motion of electrons in a wire which creates an extra signal not originally sent by the transmitter. Induced noise comes from sources such as motors and other electronic appliances. These devices act as a sending antenna, and the transmission medium acts as the receiving antenna. Crosstalk is the effect of one wire on the other. Impulse noise comes from power lines, lightning etc. | ||||||||||
Describe composite single.Composite Signals are the combination of more than one sine waves. Simple sine waves can be used to carry electric energy from one place to another or we can use a single sine wave to send an alarm to a security center when a thief opens a door or window in the house.A single frequency sine wave is not useful in data communications we need to send a composite signal. A composite signal can be periodic or non-periodic. The figure of composite periodic signal is given below. 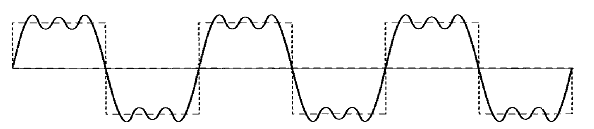 | ||||||||||
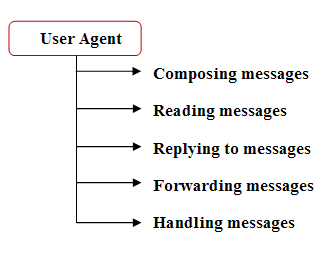
Describe MIMEElectronic mail has a simple structure. It can send messages only in NVT 7-bit ASCII format. It cannot be used for those languages that are not supported by 7-bit ASCII characters so languages such as French, German, Hebrew, Russian, Chinese etc cannot use this format. Also, it cannot be used to send binary files or video or audio data.We need a protocol that allows non-ASCII data to be sent through e-mail. So Multipurpose Internet Mail Extensions (MIME) is the answer. MIME transforms non-ASCII data at the sender site to NVT (Network Virtual Terminal) ASCII data and delivers them to the client MTA to be sent through the Internet. The message at the receiving side is transformed back to the original data. Main task of MIME is to transform non-ASCII data to ASCII data and vice versa. 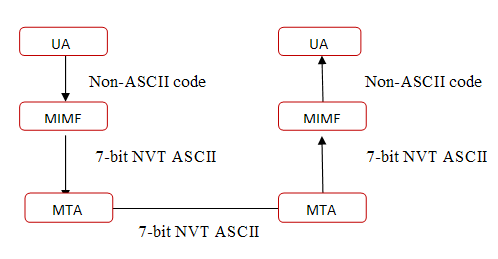 MIME header Multipurpose Internet Mail Extensions defines five types of header. 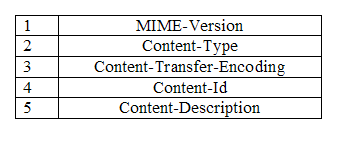 | ||||||||||
SMTP is push protocol Justify your answer.SMTP is a push protocol; it pushes the message from the client to the server. For sending email SMTP is used two times, between the sender and the sender's mail server and between the two mail servers. To send mail, a system must have the client MTA (Message transfer agents), and to receive mail, a system must have a server MTA. SMTP uses commands and responses to transfer messages between an MTA client and an MTA server. Commands are sent from the client to the server and Responses are sent from the server to the client. SMTP is not used in pulling the message.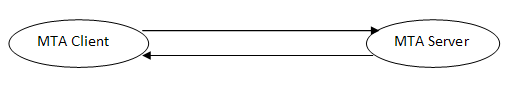 | ||||||||||
Describe the POP3 protocol.Post Office Protocol, version 3 is used for accessing the message. POP3 is very simple protocol and has limited functionality. POP has different version but currently version 3 is used. A POP3 server listens on well-known port 110. POP3 supports two types of mode.Delete Mode: In this mode, the mail is deleted from the mailbox after each retrieval. Keep Mode. The mail remains in the mailbox after retrieval. | ||||||||||
Describe IMAP4 (Internet Mail Access Protocol) in detail.This protocol is also used in Internet for accessing the mail. IMAP4 has more feature than POP3 and is more powerful.Main difference in POP3 and IMAP4 are as follows. 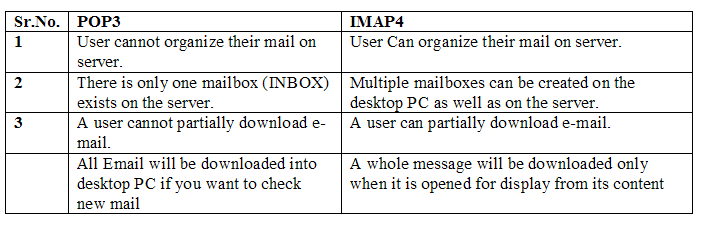 | ||||||||||
What is Anonymous FTP?Some sites provide the functionality that user can access the file with limited access. To access these files, a user does not need to have an account or password. For using FTP, the user enters "anonymous" as a user ID and guest as password. Usually, you can enter anything as a password.
|
Popular Posts
-
Biggest advantage of OSPF over EIGRP is that it will run on any device as its based on open standard Advantages It will run on most ro...
-
OSPF Definition: Open Shortest Path First (OSPF), It is a routing protocol used to determine the correct route for packets within IP n...
-
. With which network type will OSPF establish router adjacencies but not perform the DR/BDR election process? A. Point-to-point B. ...
-
Q1. What are 10Base2, 10Base5 and 10BaseT Ethernet LANs? Ans. 10Base2 —An Ethernet term meaning a maximum transfer rate of 10 Megabits pe...
-
Introduction This document describes how a router that runs Open Shortest Path First (OSPF) selects a router ID, in what packets this va...
-
Describe Domain Name System. There are two types of client/server programs. First is used directly by the user, such as e-mail, Seco...
-
Difference between RIPv1 and RIPv2? How many number of routes carried by RIP packet? Is OSPF link state or distance vector or path vecto...
-
Practical Exercises are designed to test your knowledge of the topics covered in this chapter. The Practical Exercise begins by giving yo...
-
Border Gateway Protocol is an exterior gateway protocol, which is different from the interior gateway protocols discussed so far. The dist...
-
Network Engineer is a higher-level position, often with a “junior” or “senior” prefix. The major responsibility of a network engineer is ...
Saturday, 13 February 2016
interview question for network administrator 6
Subscribe to:
Post Comments (Atom)
No comments:
Post a Comment